This is a TLS scanning server
It is used to determine the TLS handshake behavior of high-profile HTTPS websites (e.g. those in the Alexa Top ranking). This is part of the ongoing AutoSCA research project and operated by the ITSC research group of the University of Wuppertal. If you want to be excluded from any future scanning activities, please use the information below to get in touch.
How do I exclude my domains from this scan?
To have your host or network excluded from future scans conducted by us, please contact jan.drees@uni-wuppertal.de and include the domains or IP addresses/subnets you would like us to blacklist.
Alternatively, you can configure your firewall to drop traffic from the single IP address we use for scanning: 132.195.214.242
Do I need to worry?
We will never attempt to exploit security problems, guess passwords, or change device configuration. We only receive data that is publicly visible to anyone who connects to your TLS server. We send TLS handshakes with invalid RSA padding, which may result in a "Warning" entry in your server log. Even though the requests this server sends look similar to a Bleichenbacher attack, we do not execute any actual attack, neither on messages or keys. If our analysis reveals that a server is running a vulnerable TLS software, we will notify the server administrator as soon as possible.
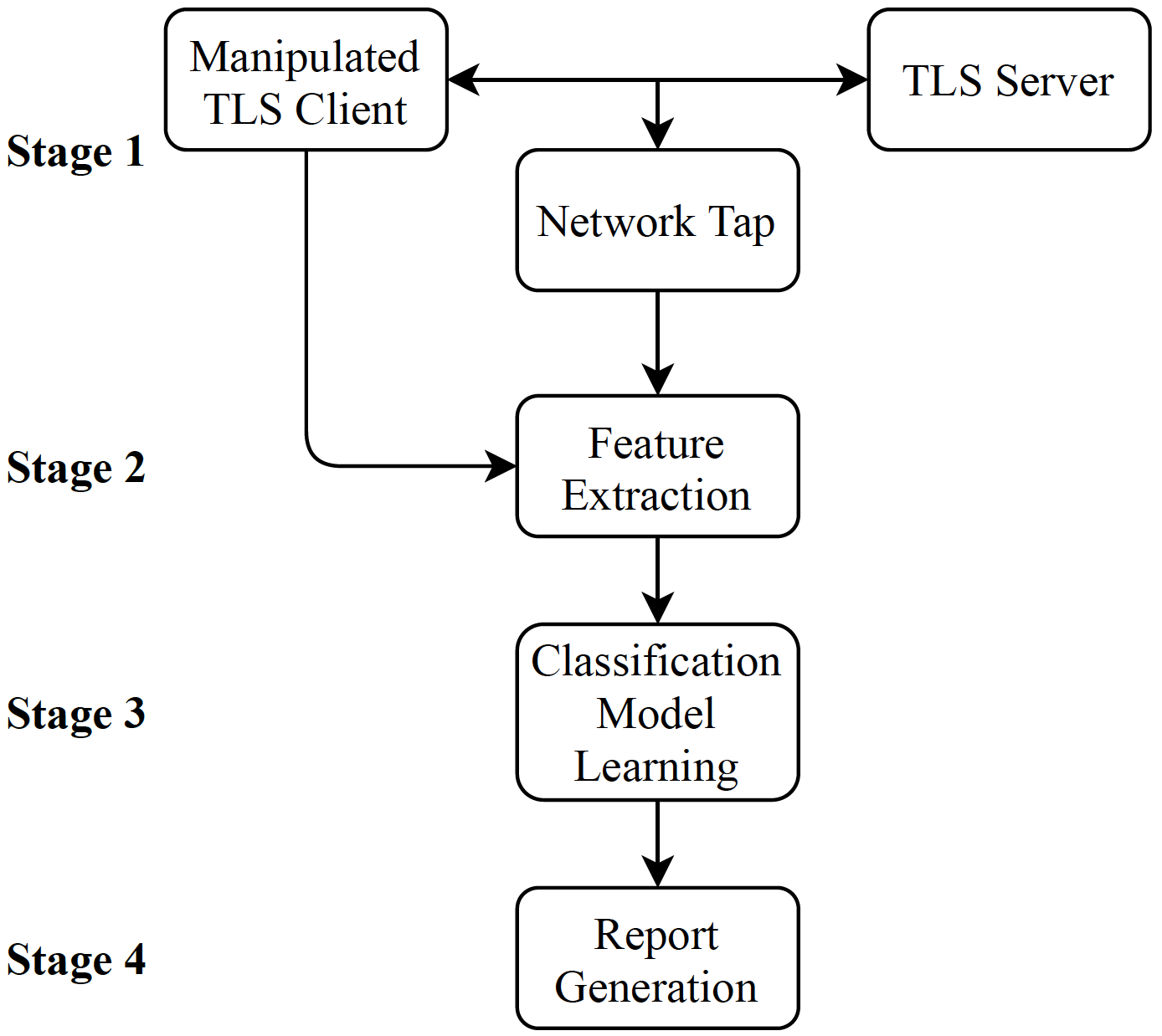
What does this server do?
This server executes thousands of RSA handshakes with each target web site. Each handshake uses one of several handshake manipulations, where the RSA padding does not conform to the PKCS1v1.5 standard. The response of the server is recorded with tcpdump and analyzed using machine learning. This process detects if the server is vulnerable to a Bleichenbacher-like side channel.




